In security , I’ll explain how to configure SAP Hana authentication method based on:
For my setup I’ll use my lab environment based on VMware, Microsoft Server 2008 R2, SAP Hana Rev 101 on SLES 11 SP3 and Windows 7 Enterprise.
Disclaimer: For my deployment I’ll issue local certificate with no outside exposure.
In order execution
1813724 - HANA SSO/Kerberos: create keytab and validate conf
1900023 - How to setup SAML SSO to HANA from BI
Link used
Help SAP Hana Platform Core - Security
Overview Architecture
- Hana SSO with Kerberos authentication
- Single Sign-on with SPNEGO
For my setup I’ll use my lab environment based on VMware, Microsoft Server 2008 R2, SAP Hana Rev 101 on SLES 11 SP3 and Windows 7 Enterprise.
Disclaimer: For my deployment I’ll issue local certificate with no outside exposure.
In order execution
- Register SLES server into DNS
- Step-by-step check on Hana server
- Create Hana Database service user in AD
- Register service Principal Name (SPN) in AD
- Generate the keytab file
- Configure Kerberos from Hana studio
- Configure SPNEGO for XS application
1813724 - HANA SSO/Kerberos: create keytab and validate conf
1900023 - How to setup SAML SSO to HANA from BI
Link used
Help SAP Hana Platform Core - Security
Overview Architecture
The following architecture is based on virtual server, below the information detail for my deployment:
• Domain: will.lab
• Active Directory and NTP server: activedir.will.lab / 192.168.0.109
• Hana server: vmhana01.will.lab / 192.168.0.116
• Desktop client: desk-client.will.lab / 192.168.0.137
Register SLES server in DNS
Registering your Linux server into my DNS will make easier the management of the entire landscape, but to make the registration successful several prerequisite needs to be respected:
• The network card needs to be setup according the dns entry
• The Linux server must have the same time zone as the DNS
The necessary configuration can be done by the tools “yast or yast2” or by command line, I will use Yast2 to make it
Specify the DNS server ip in “Name Servers” and the domain in “Domain search”
My ntp server is my Active Directory server
Once done, form network service, select “Windows Domain Membership”
As you can see I did not put “will.lab” but “will” only, then choose the option you want to propagate and hit ok to validate
Once reached out the administrator password is needed to join the domain, put it and hit “obtain list” to make sure the password is ok
We are now part of the domain
To validate I’ll make two test, I’ll fist make an nslookup from linux server on the my client desktop
And the second one is on my client desktop, I’ll ssh my linux server and connect to it with my ad user
Step-by-step check on Hana server
The registration on Linux server done into my AD is the first step, now I need to perform a series of internal check to guaranty a successful configuration.
It consist of:
- Hostname resolution check
- Hana database server krb5.conf file check
Run the following command and make sure you have the exact result as below with your information
And also check the reverse lookup
The registration in AD changed the entry the krb5.conf file, add the following line
And make two test with “kinit” and “klist” tool
Create Hana database service user in Active Directory
The check done with the expected return value, I need now to create a service users in active Directory to represent Hana database which will be map as SPN.
I’ll create those service in a dedicated OU in to grant necessary administrative privileges
I used the command line, but it could also be created from tool in AD :
dsadd user "cn=vmhana01,OU=hana,DC=will,DC=lab" -pwd <password> -disabled no -pwdneverexpires yes -acctexpires never
Now make a connection test from Hana server by using “kinit” tool
Register Service Principal Name (SPN) in AD
In this step I will now map a service name to my service user created earlier, in case of Hana the format must be respected as follow:
hdb/<DB server>@<domain>
I use the following syntax in AD to generate it : setspn -S hdb/vmhana01.will.lab WILL\vmhana01
Generate the keytab file
In elevate mode run the following ktpass command:
ktpass -princ hdb/vmhana01.will.lab@WILL.LAB -mapuser WILL\vmhana01 -ptype KRB5_NT_PRINCIPAL -pass <password> -crypto All -out c:\krb5.keytab
Take in note kvno number, in my case “3”
The consistency check can also be done by using the python script “hdbkrbconf.py” provided in the note: 1813724 - HANA SSO/Kerberos: create keytab and validate conf
Configure Kerberos for Hana studio
The SPN done by the command above did create a keytab on my windows server, I’ll copy it into my Hana server at /etc and check the content
And verify the consistency of the keytab in order to prepare the “kvno”
The kvno valid I create test user in Active Directory and try to log with it in Hana studio.
I did use the command line but you can also create it by the graphic tool
Now create I go in studio as “SYSTEM” or a user with administrator privilege to map my test user account for Kerberos
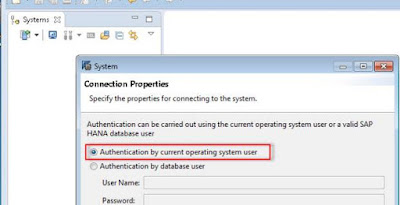
Once done i’m logging my test account on my client desktop and add the Hana entry with the “Authentication by current operating system user” option
And I’m in without password
Configure SPNEGO for XS application
To configure SPNEGO for XS application a new SNP needs to be created, earlier I did use the following format “hdb/<DB server>@<domain>” for the studio connection, but for HTTP connection the following format needs to be used:
HTTP/<DB server>@<domain>
I’ll map the same service user created earlier “vmhana01”
And reprocess the check to ensure the correct version of the kvno number
Since I’m not a developer, I’ll created test app upon the developer guide tutorial section 2.5 to test the authentication mechanism.
Here is the .xsjs application created, it display the hello text after logging
As we can see the password is required
To change the authentication behavior, from XS Admin Tool select the created project app and hit “Edit”
Specify SPNEGO and save
Note: I did specify SPNEGO for the all package, but it can be also set with more granularity
And try again and it works
Note: I’m using Mozilla, so use the specific add-on for NTLM Integrated Authentication
The configuration is completed for my Kerberos/SSO
Source: scn.sap.com



























No comments:
Post a Comment