In this article I will explain how these federated roles from S/4HANA assigned automatically to users in BTP via SAP Identity provision service without any manual intervention.
To achieve this scenario, we should have below prerequisite: -
- SAP BTP cockpit, where we subscribe to the Cloud Identity Services connectivity plan in the subaccount.In SAP BTP Cockpit, open the subaccount and choose Service Marketplace Integration Suite- Cloud Identity Services and then choose for what type of tenant (test or productive) to use in the subaccount.
- The Identity Provisioning section of SAP Cloud Identity Services administration console, where we configure the S/4Hana system and SAP IAS as provisioning system.
- Content Federation has been setup and S/4HANA role content are federated and visible as role collection in BTP.
Below are the configuration Steps for automatic Federated role assignment in BTP Via SAP Identity provision service.
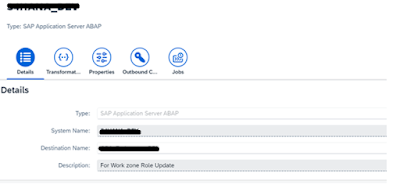
1. Create a destination for S/4Hana as Application Server ABAP system.
Open SAP BTP cockpit, and in the Identity Provisioning subaccount create a destination for the AS ABAP system. The destination configuration is required by the Identity Provisioning service to find the back-end system to be used for reading data. It also provides the credentials of the technical user (created in S/4Hana System), needed for the connection to the ABAP public API.
2. Create Source System as S/4HANA system.
Access Identity Provisioning. Add SAP Application Server ABAP as a source system. From the Destination Name dropdown, choose the RFC destination we have created in Step 1.
Read the users from Source S/4HANA based on the Federated Role assigned to users in S/4HANA system.
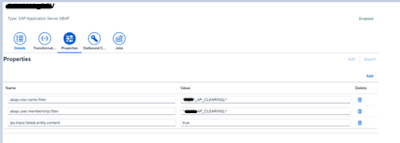
Add the Federated role in the User filter source system.
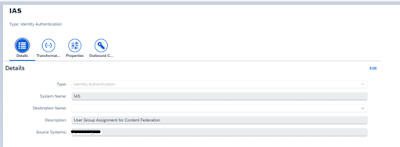
3. Create target system as SAP IAS
Add Identity Authentication as a target system and keep source system the same as created in Step 2. Set up the communication between Identity Provisioning and Identity Authentication and configure the authentication method. I have used basic authentication.
For basic authentication, provide a password. The user ID will be generated automatically when we set the password for the first time.
a. Add system as administrator and provide the respective credentials. Make sure Manage Users and Manage Groups authorization roles are enabled for the technical user. This way, we can create, edit and delete users and groups in the Identity Authentication user store.
Please put below mandatory property also other respective properties as required.
|
ias.user.unique.attribute |
This property defines by which unique attribute(s) an existing user will be resolved in the event of conflicting users. Its value is set to emails[0].value, since we are using common attribute as email for user. |
| User |
For BasicAuthentication Enter the Client ID of the Identity Authentication technical user created in step 3(a). For example: 1ab7c243-5de5-4530-8g14-1234h26373ab |
| Password |
Enter the Client Secret of the Identity Authentication technical user. It is generated automatically for the administrator of type system, when choosing Secrets. |
Note: - In our case we have different login name in S/4 Hana and SAP IAS and same email address is maintained in both the applications. SAP IAS has existing user master record based on SuccessFactors.
In this case IPS jobs with patch operation will make sure no information of existing IAS user will get change and it will patch the login name in display name of the S/4HANA user in SAP IAS.
Add the below transformation to perform Patch operation based on email Id since username in IAS is different from the one in S/4HANA system, so email ID is used. S/4HANA Login name will be updated in display name field in IAS.
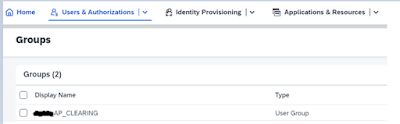
4. Create IAS group with same name as S/4 Hana Roles.
Create User group in SAP IAS with the same name as S/4HANA roles. Since the same group name will be mapped to users based on the transformation scripts.
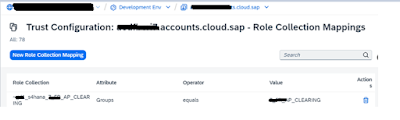
5. Map Role collection
Once S/4Hana Fiori roles are federated to BTP, they are visible as BTP role Collection. Map these federated roles with IAS group created in step 4 in BTP trust configuration for the IAS configuration subaccount.
6. Run the IPS synchronization Job.
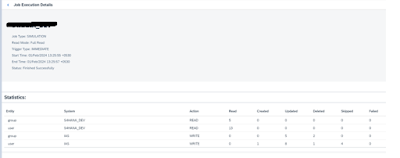
Run the Read job for the Source S/4HANA created in Step 2. This job can be scheduled in regular interval to read the users from S/4Hana and write in SAP IAS.
Job Logs will show the user and group – created/ updated/Deleted based on the source and target transformation scripts.
7. SAP IAS group assignment.
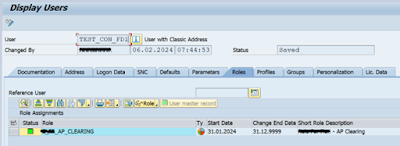
In SAP IAS user will get the IAS group automatically assigned once the IPS synchronization job gets finished. User will be getting the groups assigned based on the role assigned in S/4Hana.
a. Role Assigned in S/4HANA.
b. Same groups get assigned to user in SAP IAS automatically based on the Role assigned to user in S/4HANA in Step 7(a).
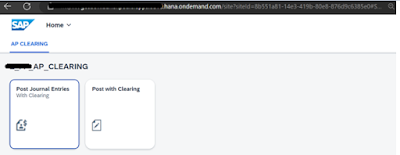
8. Login with the same user id’s email in SAP BTP Work zone site.
User can login to work Zone site and access the application federated by S/4 HANA roles.





No comments:
Post a Comment