Preamble: Being an SAP technology consultant, throughout my career I have been getting so many helps from the contents written by the experts of SAP Community , hence I thought this is the pay-back time.
If you are well aware of the architecture of SAP HANA Platform and Kerberos , then needless to say this SSO works for a SAP HANA Scale-out system as well. But when I had implemented it for a customer , I found it hard to find any relevant documentation that could’ve supported my understanding and made my life bit easy. So, as I dealt with it already ,here I am with this blog , that will depict the exact configuration steps for the aforesaid to move forward.
SSO , Kerberos and SAP HANA: Single Sign-On allows a user to log on once and gain access to multiple resources without being asked to produce credentials repetitively. Kerberos is a network authentication protocol based on secret key cryptography, originated by MIT scientists. SAP HANA supports Kerberos v5 for single sign-on based on Active Directory (Microsoft Windows Server) or Kerberos authentication servers.
I am not going into the theoretical details of SSO and Kerberos and as many experts had already come up with excellent documentations for each of the topic. In this blog, I will remain focused onto the SAP HANA Scale-out configuration steps for the same.
Example scenario: Let us assume a SAP HANA Scale-out engine having 4 Active nodes and 1 Standby node being used for Production workloads. Essentially you are using default failover solution for SAP HANA Scale-outs.
So now if you want to implement SSO to that SAP HANA engine by Kerberos, you may feel sufficient configuring SSO to your Acting Master Node to get your requirement accomplished . But what if your Acting Master Nodes crashes and one of the other Master nodes becomes the acting master node ? Eventually the failover would be automated and should result into no data loss but switching your master node will lead to breakage of Single Sign-On to the users who were actively using that SAP HANA engine.
Hence you come up with a node redundant SSO solution that can deal with SAP HANA auto host failover. If I reframe it, then you have to configure Kerberos SSO to each of the nodes of the SAP HANA engine so that if failover happens, then also users can access SAP HANA engine by logging into other SAP HANA worker nodes through Single Sign-On.
Configuration and descriptions: To allow users to log on to the SAP HANA Scale out database from a client using Kerberos authenticated SSO, the following configuration steps are necessary:
1. FQDN test and Reverse Lookup test
2. Check and install Kerberos packages if needed
3. Create service user in AD (Active Directory), map SPN
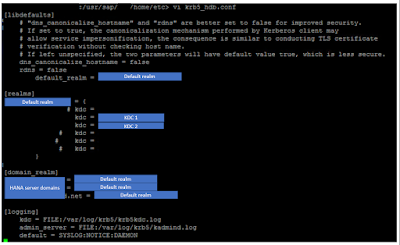
4. Maintain Kerberos Configuration file across nodes
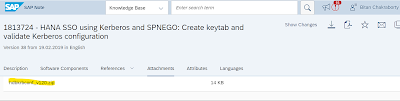
5. Get automation script from SAP Note : 1813724 – HANA SSO using Kerberos and SPNEGO: Create keytab and validate Kerberos configuration
6. Configure Kerberos
7. Copy generated keytabs in each SAP HANA nodes
8. Reboot SAP HANA
9. Perform user mapping
10. Update client tools if required
11. Test
Now let’s go through little bit details of each one stated above :
1. FQDN test and Reverse Lookup test: First you are going to see by which FQDN and IPs your SAP HANA servers are sitting in, easiest way to perform the following:









No comments:
Post a Comment