Principal propagation gives the ability to forward the user context of the message unchanged from the sender to the receiver.
In this blog post, lets discuss on how to implement SSO with principal propagation in a way that it trusts the requests coming via the cloud connector configured.
There are two levels of trust that needs to be configured. First, the Cloud Connector needs to identify itself with the system certificates for the HTTPS. Second, we need to allow this identity to propagate accordingly, so that a short lived X.509 certificate could be forwarded.
Finally, we map the user in the target system – the SAP S/4HANA on-premise system, in this case.
The X.509 certificate contains the information about the cloud user in the subject and this information is needed for mapping the particular user to the corresponding user in the target system.
Step 1 – Generate Certificates in Cloud Connector
Luckily, from Cloud connector version 2.12.3, we no longer need third party tools to generate the certificates.
We have to configure three certificates in Cloud Connector.
1. System Certificate
2. CA Certificate and
3. User Certificate
1.1 System Certificate
To configure the System Certificate, go to ‘Configuration’ and choose the ‘On Premise’ tab. Click on the “Create and import a self-signed certificate” button under System Certificate.
Fill the required details in the pop-up window. The Common Name (CN) represents the server name protected by the SSL certificate. The request hostname has to match the certificate Common name for valid certificate.
Download the generated certificate.
The downloaded sys_cert.der certificate will be used in the later steps. It will be uploaded to the SAP S/4HANA on-premise backend system (STRUST).
1.2 CA Certificate
A CA certificate signs all the certificates which are used when a request is forwarded from the cloud with the cloud principals.
To create the CA certificate, scroll down to the corresponding section and click on the “Create and import a self-signed certificate” button.
Fill the required details in the pop-up window as explained above to generate the certificate.
The Cloud connector acts as a CA when the request is sent from the Cloud Platform to SAP S/4HANA On-premise system. Every request from the Cloud Platform will be signed from Cloud Connector with that certificate. SAP S/4HANA needs to trust this certificate to establish the communication from cloud to the On-premise system.
1.3 User Certificate
Scroll down to the Principal propagation section.
Edit the Subject Pattern
Select the Subject pattern from the list to assert the user ids. For example, Select ${mail} to assert the user against the user’s mail address propagated from the Cloud.
Note: Depending on the assertion attribute, you can select the subject pattern. You can also provide manual pattern, if it is not listed in the dropdown. For example ${email}
Now, click on the Create Sample certificate button
This sample certificate is used to define the rules in the SAP S/4HANA On-premise system under the Transaction code (CERTRULE).
Step 2 – Synchronize the Cloud Subaccount IDP
Go to “Cloud to On-premise” setup and the Principal Propagation Tab.
Click on the Synchronize button to sync the Trust Configuration details of the connected subaccount.
Step 3 – Configure backend system details in cloud connector
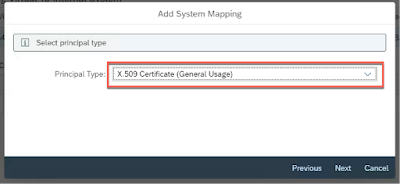
Create a new System Mapping. Provide the Internal and Virtual host details.
Choose the Protocol as HTTPS and Principal Propagation Type as X.509 Certificate (General Usage).
After adding the system mapping, add the Resource access policy.
Step 4 – Configure SAP S/4HANA On-premise backend system with certificates for the Principal propagation setup
To do the necessary configurations, we need to perform the following steps
◉ Import the System certificate downloaded from the Cloud connector into the SSL Server standard (Transaction code – STRUST)
◉ Define the rule-based mapping by importing the Sample certificate downloaded from Cloud connector. (Transaction code – CERTRULE)
◉ Maintain the reverse proxy parameters in the Default Profile. (Transaction code – RZ10)
◉ Restart the ICM and check the profile parameters. (Transaction code – SMICM)
4.1 Import the System Certificate
Go to the transaction code STRUST
Expand the SSL Server Standard and go to the Instance specific as shown in the below image. If there is no existing SSL Server Standard, switch to the Edit mode and right click the SSL Server standard to create one.

Click on the Import Certificate button to import the System certificate downloaded from the Cloud connector (sys_cert.der). Click on “Add to Certificate list” button to add the certificate to the list of trusted certificates
4.2 Define the Rule based mapping
Go to the transaction code CERTRULE.
Click on the “Import Certificate” button to import the Sample certificate (scc_sample_cert.der) that we downloaded from the Cloud connector in section 1.3
Click on the “Rule” button to map the rules
Choose the “Certificate Attr.” And Login as E-Mail (or User Name as per the requirement).
Once saved, you can notice the Status in the right side.
4.3 Maintain Profile Parameters
Go to the transaction RZ10
Choose Profile DEFAULT and the click the Edit button for Extended Maintenance.
Click on New Parameter button
Give the Parameter name as “icm/trusted_reverse_proxy_0” and value as
SUBJECT=”CN=<>”, ISSUER=”CN=<>”
You can copy these values from the Cloud connector System Certificate section
After, filling the values, click on the “Copy” button
Go back and click on the Save button to save the parameter and activate the DEFAULT profile.
You can ignore the Error Check validations at this point.
4.4 Restart the ICM
Go to the transaction SMICM
You can restart the ICM to reflect the changes related to the PROFILES and parameters.
Go to Administration > ICM > Hard Shut Down > Global





















No comments:
Post a Comment