I will explain and detail how to manage SAP Hana 2.0 SP2 instance with SAP LaMa 3.0 SP5 in the context of hybrid landscape between on-premise and Microsoft Azure.
In order to monitor my hybrid solution i will explain how to configure Solution Manager 7.2 accordingly.
Aside of the SAP components, I will also covert the network implication to realize such type of configuration, which include the IPSec connection between my lab and Azure by using pfSense and the DNS portion for the naming resolution between both site.
For my setup, I will use my own lab on VMware VSphere 6.5 U1, use SAP LaMa 3.0 SP5, SAP Solution Manager 7.2, Pfsense 2.4.2 and use my own Microsoft Azure subscription.
This picture shows in detail the components deploy on each server such as add-on as well as product version, the protocol of communication is showed too but I intentionally omit to provide any port.
In order to monitor my hybrid solution i will explain how to configure Solution Manager 7.2 accordingly.
Aside of the SAP components, I will also covert the network implication to realize such type of configuration, which include the IPSec connection between my lab and Azure by using pfSense and the DNS portion for the naming resolution between both site.
For my setup, I will use my own lab on VMware VSphere 6.5 U1, use SAP LaMa 3.0 SP5, SAP Solution Manager 7.2, Pfsense 2.4.2 and use my own Microsoft Azure subscription.
Components details
This picture shows in detail the components deploy on each server such as add-on as well as product version, the protocol of communication is showed too but I intentionally omit to provide any port.
From a detail components point of view, in order to ensure a transparent and secure connectivity between my on-premise environment and Azure I will use and configure PFsense and Azure Gateway to create a VPN IPsec tunnel.
The management of my SAP Hana instance is done through SAP LaMa 3.0 SP5, which will include the Azure Connector to interact with Azure VMs.
Solution Manager 7.2 SP6 is used for advanced integration monitoring for my hybrid solution.
To ensure reliability in term of naming resolution, two DNS are configured and replicated as read-only to each other.
Configure the IPsec VPN with Azure
From a topology point of view my picture below show how my network is setup on a high-level standpoint
On the left side of the picture, I have configured my VMware DvSwitch which operate for 2 different subnets, one is configured for vLan (Local) for my local server network, and the other one for vWan (Firewall) for internet access.
In order to setup my vpn, I have installed pfSense which act as a virtual firewall/router.
My pfSense is configured with 2 NIC card, one for WAN network to provide internet access to my VMs within my vLan network through the second NIC card LAN which act as a gateway.
On the right side of the picture, on Azure I will configure multiple component to create the vpn connection associate such as, virtual network and subnet, virtual network gateway and the local network gateway.
Let start with Azure configuration by creating the virtual network and subnet
My vNet range is 10.0.0.0/23 and my subnet range is 10.0.0.0/24
Once create, I select my new create vnet and select “Subnet” to create the gateway subnet
And define my Gateway subnet as 10.0.1.0/24
Now let’s create my virtual network gateway, select virtual gateway from the service marketplace
I specify the name of my gateway and choose VPN with Route-based vpn type, because I don’t need high bandwidth I select the basic SKU. I map my gateway to my virtual network created earlier and create the public IP
Note: the creation of the gateway can take up to 45 min
Once created
Finally, I will create my local network gateway
I provide a name for my local gateway, enter my public IP and gives my internal local address space where the vm needs to be reached out
Once created, I select my newly created local network gateway and click on connection to assign the virtual network gateway and set my shared key which will be use with my pfsense.
Now completed, I will configure my pfsense. On the web interface I select VPN –> IPsec
Click on Add P1
In the general information, I use WAN for Interface option and provide the Azure Gateway public ip address
For authentication method I select Mutual PSK and provide the Pre-Shared Key setup in Azure while creating the local gateway
And finally, for the algorithms, I specify AES 256 with SHA256 and save the configuration
Once done, one the created connection I click AddP2
In the general information, I choose LAN subnet for local network and for remote network I specify the address range configure previously for my Azure vNet
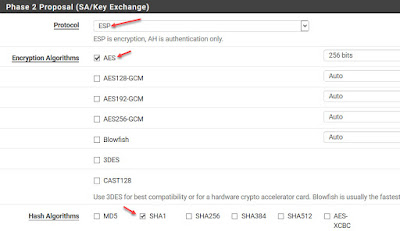
And finally, on the SA/Key Exchange, I define the protocol as ESP with encryption algorithms AES256 and hash algorithms SHA1 and save my configuration
My setup is done
Let’s have a look at the IPsec status first from pfsense
And from the Azure site and see the status of my connection
My vpn connection is fully configured, I will do a quick check from my local network to azure
It works I can RDP from my local network to Azure by using the private IP, this first part completed I will configure my DNS in order to resolve mutual domain and hostname.
Setup DNS for mutual name resolution
My hybrid scenario consists of using Azure as a DR site, to do so I have install two DNS with two distinguish FQDN.
My local FQDN is mtl.will.lab and Azure is us.will.lab
To make the resolution both ways, on the primary DNS I right click on my primary zone and click on property, then I select Zone Transfers and add the ip of my Azure DNS server
And do the same for the reverse lookup zone
Now on Azure, I go on my secondary DNS server and proceed the same way
Now I go back on my primary DNS (local) and define a secondary Forward Lookup Zones to match my Azure domain
And do the same in the Reverse Lookup Zone
I have proceeded with the same step on the Azure DNS server
So now from my local network I will try to resolve the Azure FQDN, to do so i have add a temporary entry to make a quick test
Now from my local server I will nslookup and it’s working
My DNS resolution is working on both side, now I can configure SAP LaMa Azure connector











































No comments:
Post a Comment